Today’s Technical Tuesday post summarizes multi-factor authentication techniques and explains strategies and best practices for implementing multi-factor authentication in Acumatica cloud ERP.
Security conscious businesses require multi-factor authentication to verify user identities before allowing them to access sensitive ERP data. Acumatica cloud ERP provides mechanisms to support multi-factor authentication to prevent unauthorized system access.

Multi-factor authentication options
Multi-factor authentication involves two or more authentication mechanisms. A list of authentication options is listed below.
- Username / Password
- The most basic authentication mechanism requires users to enter a username and password.
- Additional options such as IP address validation and strong password requirements provide additional security.
- Token, FOB
- Users carry a token device that displays a code that is regularly updated. The user types the code into the ERP (Enterprise Resource Planning) system which verifies the code. RSA SecurID tokens are an example.
- Mobile Phones
- The ERP system sends a text message to the user’s mobile phone. The user verifies their identity directly on their phone or by entering an access code in the application on the device they are using to access the ERP system.
- Another option is to install a secure application on the phone that behaves like a token.
- Email
- During login, the system sends a code to the user’s email address. The user enters a code in the email to authenticate.
- Smart Card or USB Device
- Hardware issued by the organization can be configured to grant access when a card is swiped or when a USB device or chip is inserted.
- Fingerprint Reader or Biometric Device
- Biometric devices work like smart cards. They require an initial setup but cannot be lost or stolen.
- VPNs
- The VPN has its own authentication mechanism which provides a layer of security at the communication level. VPNs can be authenticated using passwords, tokens, mac addresses, and other methods.
By combining two mechanisms above, businesses can achieve two-factor authentication. Most two-factor mechanisms require something you know (password) plus either something you have (token, mobile phone, USB) or something you are (fingerprint or other biometric).
Adaptive (smart) multi-factor authentication
Often there is a trade-off between security and usability. The additional security associated with multi-factor authentication comes at the expense of users logging in twice instead of once.
To improve usability, some multi-factor systems have been configured to select multiple authentication mechanisms only when the risk profile of system entry is high. The risk profile can be set based on information gathered about the user’s environment, such as the machine MAC address, the IP address, browser cookies, time of day, and other patterns.
Some examples of risk profiles include:
- Low risk: Login from an office IP address at 9am on weekdays using a browser with a stored cookie.
- Medium risk: Login from unfamiliar IP address
- High risk: Login from unfamiliar IP address, after hours, using an unknown machine
Based on the risk level, multi-factor authentication may not be required. Machine learning can be utilized to analyze failed logins and adjust risk levels.
Multi-factor authentication in Acumatica cloud ERP
Here are the multi-factor authentication strategies in Acumatica cloud ERP.
Single sign-on
The best way to implement multi-factor authentication in Acumatica cloud ERP is to take advantage of Acumatica’s support of single sign-on (SSO) capabilities. Acumatica’s cloud ERP software currently supports SSO with Microsoft, Google, and OneLogin (requires installing a customization). These providers support multifactor authentication.
- Microsoft: Azure multi-factor authentication supports phone calls, text messages, mobile app notification, and third-party tokens. https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-mfa-howitworks
- Google: Two factor authentication via mobile phone or USB security key. https://www.google.com/landing/2step/#tab=how-it-works
- OneLogin: Free and paid two factor authentication options including one-time password app, Duo Security, RSA SecurID, and mobile options. https://www.onelogin.com/product/multi-factor-authentication
In this model, users login to a provider above using multiple authentication options. Next, the user is seamlessly signed into Acumatica using Single sign-on.

VPN
An alternative strategy involves setting up a VPN. The VPN is the first layer of authentication while the Acumatica username and password acts as the second layer.
Implementation of multi-factor authentication in Acumatica cloud ERP
Implementing multi-factor authentication is straightforward but involves several steps.
Step 1: Obtain Multi-Factor Authentication Provider Accounts
Get an account for each user who will login to Acumatica. The account must include single sign-on capabilities and the multi-factor authentication mechanism that you will utilize.
These accounts can operate independently from Acumatica for other purposes within your organization.
Step 2: Implement Single sign-on
Single sign-on capabilities must be implemented at the Authentication Provider and inside Acumatica.
First, you will need to enable SSO for the Authentication Provider. Obtain information from the Authentication Provider on how to set this up.
Next, you establish a secure mechanism to hand-off authenticated users to Acumatica. To provide a secure hand off, you implement an HTTPS connection between the two systems plus an authentication mechanism. Microsoft and Google utilize OAuth 2.0 while OneLogin uses SAML 2.0. Detailed instructions are available in Acumatica help for Google and Microsoft and via a separate document for OneLogin.
As part of establishing a secure hand-off, each system provides a certificate that can be entered into the other system. In the Acumatica Security Preferences screen, you can enter the certificate provided by the external providers as shown below.
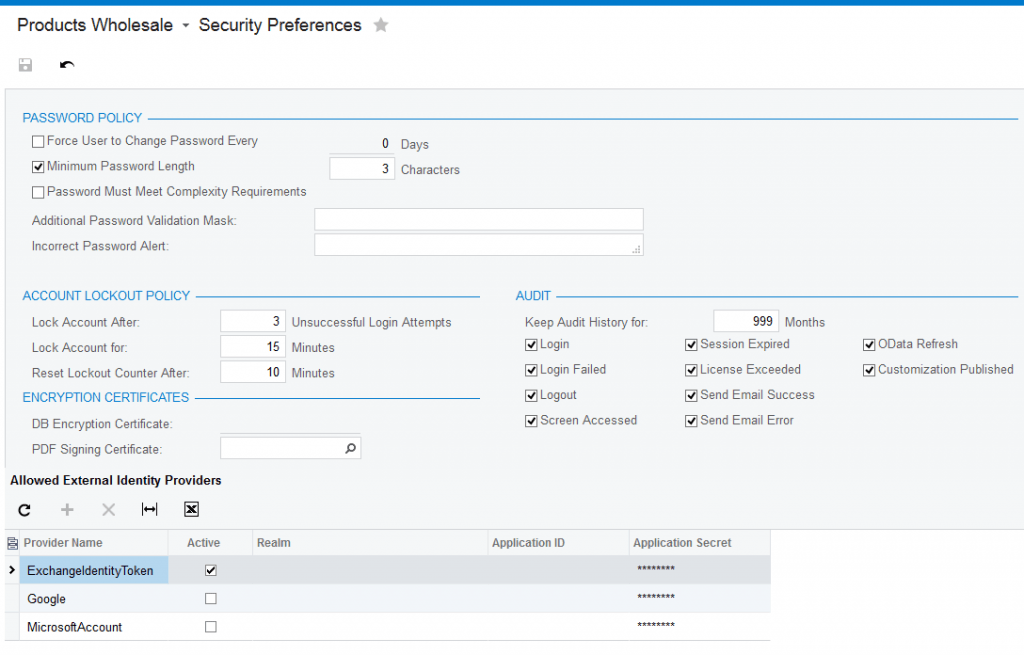
Single sign-on setup usually involves changes to the web configuration and other system files. As a result, SaaS deployments will require assistance from Acumatica.
Step 3: Modify the Login Page
To prevent people from bypassing the multi-factor authentication mechanism, remove the username and password option from the login page.
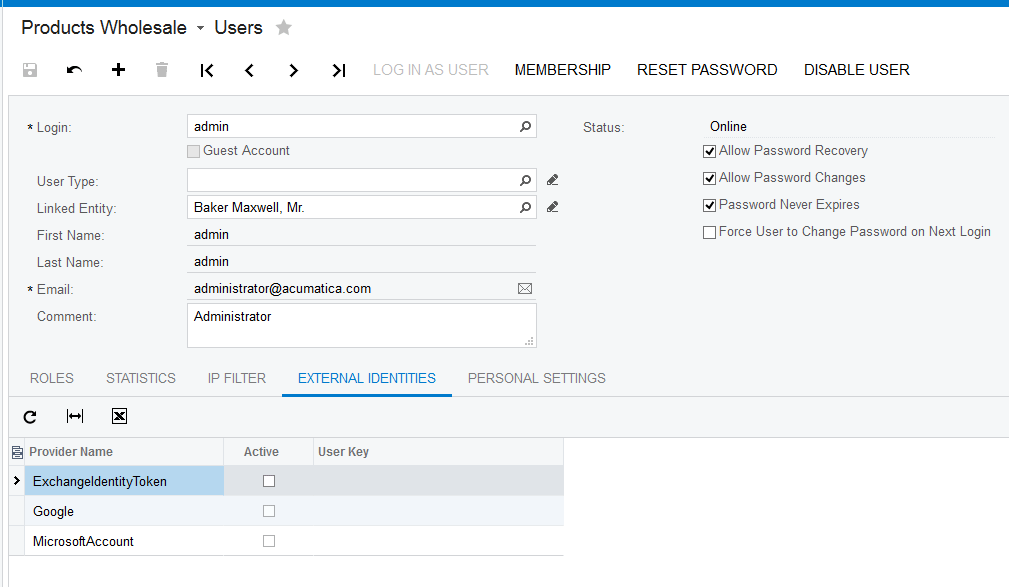
Step 4: Link External Accounts to Acumatica Accounts
When an identity is passed from an external Authentication Provider, Acumatica needs to know which Acumatica user this identity is associated with.
This linkage can be configured on the User Profile screen or the Users screen on the External Identities tab.
Multi-factor implementation costs
Implementing multi-factor authentication involves additional costs as described below.
- Multi-Factor Authentication Provider
- Authentication Provider Accounts: Each user who will login to Acumatica must have an account from the Authentication Provider. These costs may be bundled with other services (i.e. Microsoft Office 365) or available as a stand-alone account. These costs are between $2 – $10 per month per account and are billed by the external provider.
- Usage Fees: In addition to an account, there may be additional fees for usage.
- Multi-Factor Authentication Fees: Different multi-factor authentication options have different fees associated with them. For example, a token will involve an up-front hardware purchase while utilizing a mobile device may involve purchasing a Twilio/Authy account.
- Implementation Fees
- Setting up and maintaining the integration may require professional services help.
- For private cloud deployments, the Acumatica partner may include this in the overall implementation costs.
- For SaaS deployments, budget a small amount for Acumatica services.
Acumatica cloud ERP and ERP platform offers users optimum security
Acumatica cloud ERP and our modern Enterprise Resource Planning platform supports multi-factor authentication by connecting to an Authentication provider using single sign-on. The strategy allows Acumatica customers to select the authentication option that works for their budget, user complexity, and desired level of security. Some Acumatica customers utilize an alternative strategy of using a VPN on top of the Acumatica username/password to provide two-factor authentication. In the future, Acumatica may implement an internal multi-factor authentication mechanism.
Authentication technologies continue to evolve. By using the current single sign-on strategy, Acumatica can focus on developing ERP features and quickly take advantage of new biometric and adaptive technologies that improve the way security is managed.
Review our Technical Tuesday series for more informative tutorials and explanations, such as our recent posts on using Business Events to automate processes and on Acumatica’s support of accounting standards 606 and IFRS 15.
For any questions about today’s discussion on multi-factor authentication via single sign-on or about Acumatica cloud ERP and our ERP (Enterprise Resource Planning) platform, please contact us today.
Read More in the Technical Tuesday Series
—
APPENDIX: Nexvue’s Advanced Security
Nexvue has written an integration with Twilio / Authy that enables two factor authentication with a mobile phone by deploying an Acumatica customization.
The solution enables adaptive authentication based on a white list of IP addresses (so people in an office or home location do not need to perform multi-factor) and temporarily storing mobile phone authentication so external users can be challenged as administrator defined intervals.
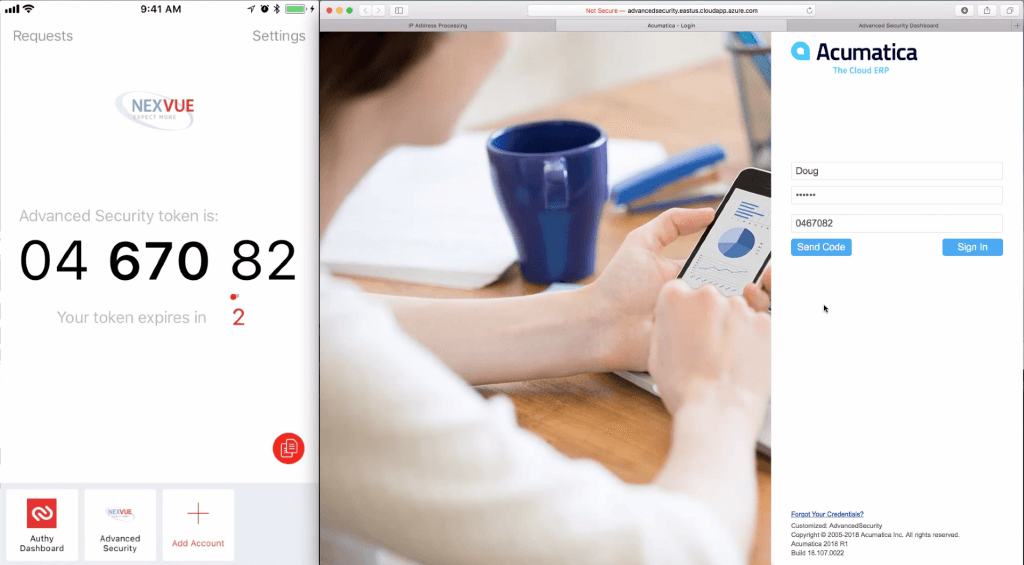
The customization includes everything you need to get started so that you are up and running with minimal professional services help. The solution does not require the Acumatica Active Directory configuration SKU.
 Canada (English)
Canada (English)
 Colombia
Colombia
 Caribbean and Puerto Rico
Caribbean and Puerto Rico
 Ecuador
Ecuador
 India
India
 Indonesia
Indonesia
 Ireland
Ireland
 Malaysia
Malaysia
 Mexico
Mexico
 Panama
Panama
 Peru
Peru
 Philippines
Philippines
 Singapore
Singapore
 South Africa
South Africa
 Sri Lanka
Sri Lanka
 Thailand
Thailand
 United Kingdom
United Kingdom
 United States
United States