Acumatica’s security model addresses multiple layers of vulnerability. Today’s Technical Tuesday article describes how data in the Acumatica cloud ERP database can be encrypted to ensure privacy and security if an intruder gains direct access to the database.

Acumatica Security Layers
Physical Security
All application code runs on the server – which can be deployed on premises or at a secure datacenter.
Transmission Security
Each session is authenticated, all communication is encrypted without the need for a VPN.
Storage Security
Data is stored on the server and encrypted. The only access to sensitive data is through the business logic.
Access Security
Object level access controls provide role-based access to specific screens, inquiries, fields, and reports. Acumatica provides federated security (SSO support with Azure AD / ADFS / Google) and two-factor authentication.
Data Security
Access permissions extend to specific accounts, sub-accounts, customers, and other objects for all screens, inquiries, and reports.
Application Security
All application code and verification logic is managed on the server to eliminate client-side data manipulation.
Acumatica’s security model protects data across all security layers (see right sidebar). This ensures that data is protected during entry, transmission, retrieval, and while at rest.
This article highlights storage security to protect your Acumatica data while it resides in the database.
Encrypting fields in the Acumatica database
Encrypting data at rest ensures privacy and security if an intruder gains access to your database. Unauthorized access includes physical access to your storage hardware or an unauthorized login to your database server.
The downside of at rest encryption is the additional processing requirements for both your database and application server. For this reason, Acumatica provides a mechanism that allows you to selectively encrypt data fields.
By default, Acumatica encrypts sensitive data such as credit card numbers, email account information, SMS account info, and passwords. Today, you’ll learn how to encrypt additional fields.
Acumatica strategy
Acumatica takes advantage of the RSA Algorithm that is part of .NET. All keys are managed behind the scenes, so it is quite easy to implement.
The data is encrypted before it is written to the disk and decrypted when read back into memory. As more and more fields are encrypted, there is more work for the application server.
Some Acumatica clients have encrypted the entire database using SQL server tools. However, this type of encryption has not been tested, so Acumatica does not guarantee that it will work. This can only be done if clients are running in a private cloud environment.
Acumatica implementation
To reduce server load, Acumatica does not encrypt all fields in the database. By using a customization project, I can add the PXRSACryptString attribute to any text field in the application and it will be encrypted.
Step 1: Create a customization project
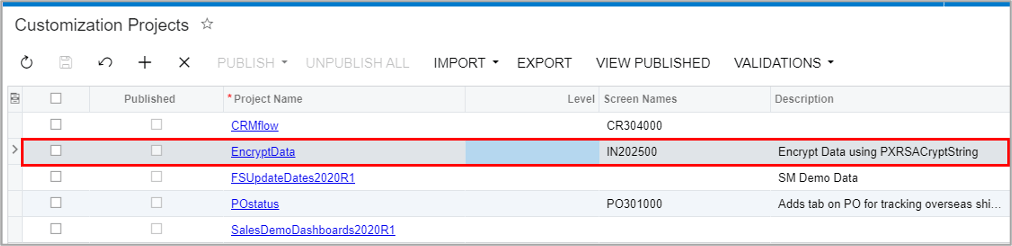
Step 2: Open project and add screens with fields you want to encrypt
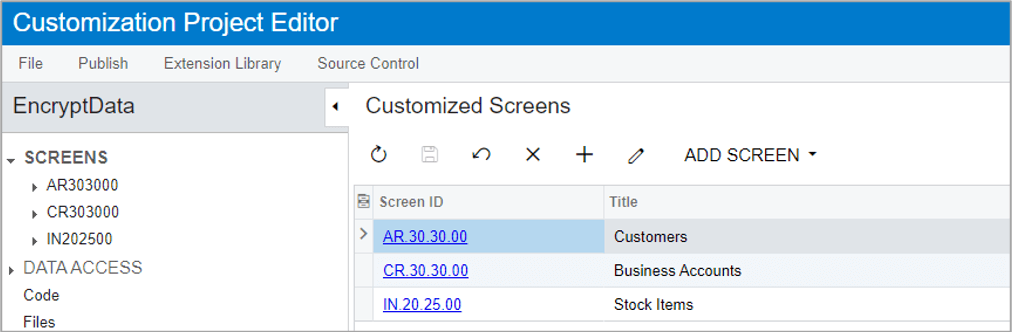
Step 3: Open screen and find field you want to encrypt
In this example, I select the Business Account Name from the Business Account screen.
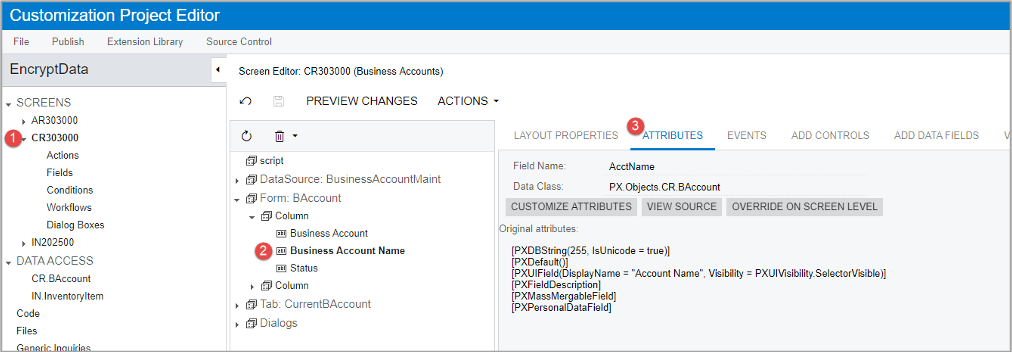
Step 4: Customize field attributes
To encrypt the field, replace the PXDBString attribute with PXRSACryptString attribute as shown below. I also added the IsViewDecrypted parameter and set it to True. If you don’t add IsViewDecrypted, then you will see only ****** in the field on the User Interface.
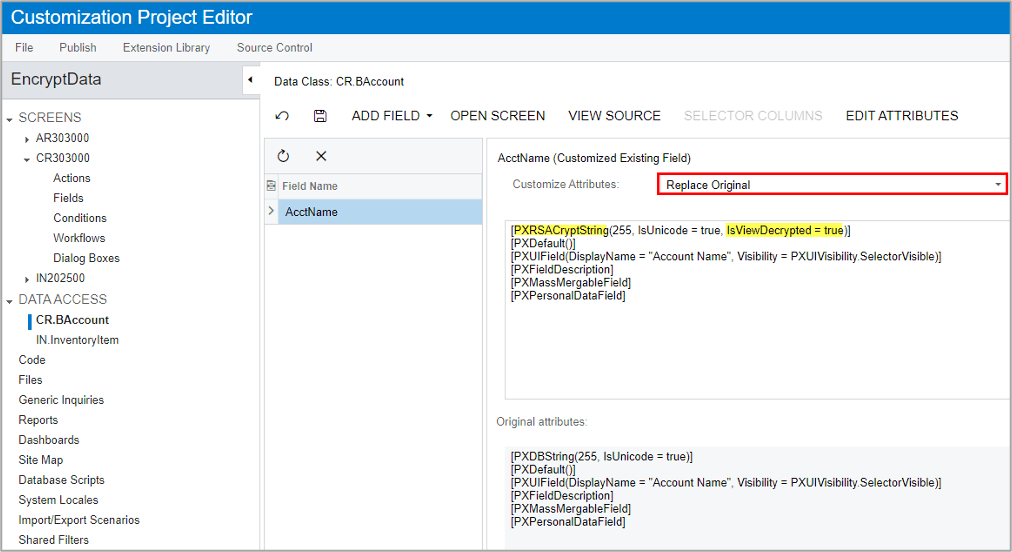
The declaration might be different in different objects. For example, in the Stock Item description, I replaced PXDBLocalizableString attribute with PXRSACryptString attribute.
Step 5: Publish your customization project
Following standard procedures, I published my customization project.
Publishing the customization does not encrypt existing data. The customization causes data to be encrypted when new data is added or when existing data is changed and saved.
When done, any new records that you add or any old fields that you change will be encrypted in the database.
Testing the results
To test my results, I opened the Business Account screen and added a new Business Account.
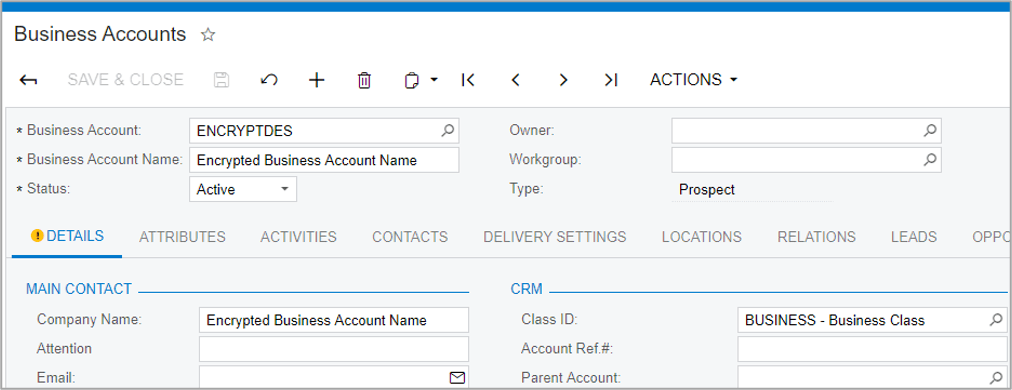
I also changed the Business Account Name on Alta Ace to Alta Ace Secure.
Next, I opened SQL Server Management Studio and created a query to view my data.
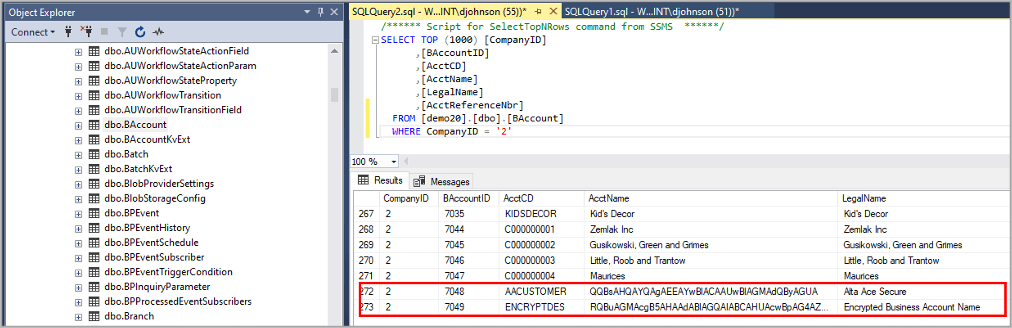
Notice that the Account Name is encrypted, so unless I access the information via the application, I will not be able to see the data.
Conclusion: Encrypting data at rest in Acumatica
Acumatica provides the ability to encrypt data as it resides in your database. By default, sensitive data is encrypted, but you can easily modify Acumatica to encrypt additional fields. This implementation allows you to selectively encrypt text data fields so you minimize server load.
Some private cloud customers have encrypted the entire database using SQL encryption tools, but this scenario is not regularly tested by Acumatica.
At rest data encryption is part of Storage Security, which is one part of a larger data security model that Acumatica has built to ensure data privacy, confidentiality, and security.
If you found this article helpful, Acumatica’s Technical Tuesday series provides even more detailed how-tos, such as how to print an MICR check or how to edit the Acumatica Portal Home Page. Contact our team with any questions or to schedule a demonstration of Acumatica’s cloud ERP software.
 Canada (English)
Canada (English)
 Columbia
Columbia
 Caribbean and Puerto Rico
Caribbean and Puerto Rico
 Ecuador
Ecuador
 India
India
 Indonesia
Indonesia
 Ireland
Ireland
 Malasya
Malasya
 Mexico
Mexico
 Panama
Panama
 Peru
Peru
 Philippines
Philippines
 Singapore
Singapore
 South Africa
South Africa
 Sri-Lanka
Sri-Lanka
 Thailand
Thailand
 United Kingdom
United Kingdom
 United States
United States